Master secure code review with our guide on techniques, tools, and best practices. Learn to build safer software and prevent costly security breaches.

Think of a secure code review like a home inspection, but for your software. You wouldn't buy a house without checking for cracks in the foundation, right? Similarly, a secure code review is the process of examining your application's source code to find security flaws before they can cause a disaster. It’s about spotting weaknesses early to build a product that’s not just functional, but strong enough to stand up to real-world threats.
In the race to ship new features, security can easily get pushed aside. It often feels like it slows things down. But skipping this crucial step is like taking on a high-interest loan; you're creating a massive "security debt" that will eventually come due, costing your company its reputation and a whole lot of money.
A proper secure code review isn't a roadblock. It's about building a solid, resilient product from the very beginning.
When a security vulnerability makes it into a live product, the fallout is never pretty. We're not talking about a minor bug that makes a button look weird. A security flaw is a wide-open door inviting attackers inside.
For a startup, a single data breach can be a killer blow. Imagine a small fintech company suffering a breach that exposes customer financial data. The QA team missed a critical flaw, and now the founders are dealing with angry users and regulatory fines instead of building their next feature. For a more established company, the damage is still immense:
Folding secure code reviews into your regular development cycle is one of the smartest moves you can make to head off these risks. It's so crucial, in fact, that the market for these tools is expected to hit $2.44 billion by 2030, growing at a rate of 14.88% each year.
The reason for this growth is simple: the return on investment is a no-brainer. Fixing a vulnerability during development is exponentially cheaper and less painful than cleaning up the mess after a public breach. You can read more about this market growth on mordorintelligence.com.
Ultimately, a good secure code review process changes the game. Security stops being a reactive headache and becomes a shared responsibility—a fundamental part of building quality software.
A truly effective secure code review isn't just about going through the motions and ticking boxes. It’s a completely different way of thinking—a mindset that weaves security into the very fabric of your development process. When you get this right, a review stops being a chore and becomes one of your most powerful, proactive security tools.
What does this look like in practice? It means your developers and product teams start seeing their own code through the eyes of an attacker. The question shifts from "Does this code work?" to a more critical one: "How could this code be broken?" That subtle change in perspective is the bedrock of a solid security culture.
If there's one skill that defines a security mindset, it's learning to think like an adversary. An attacker doesn't care about your application's intended purpose. They are laser-focused on finding ways to make it misbehave for their own benefit.
Getting into this headspace means asking some tough questions during every review:
When you start thinking this way, your team begins to anticipate exploits before they're even written. Security becomes part of the design, not just an afterthought.
Automated scanners are fantastic at flagging common, syntax-level vulnerabilities. What they almost always miss, however, are flaws in the business logic. These are the tricky bugs where the code executes perfectly but fails to enforce a critical business rule, opening the door for creative abuse.
I once saw this happen at a fast-growing fintech startup. Their app was designed for small, frequent transactions, and the code for calculating fees seemed flawless. But a subtle rounding error existed that only surfaced under very specific conditions.
A handful of clever users figured out that by making thousands of tiny transactions, they could exploit this rounding flaw to their advantage. They were siphoning off fractional cents that, over time, added up to thousands of dollars. The code was syntactically perfect, but the business logic was fundamentally broken.
This is a perfect example of why human oversight is still irreplaceable in a secure code review. A reviewer has to confirm that the code doesn't just run, but that it correctly and securely enforces the rules of the business. You can dive deeper into these kinds of scenarios by exploring some AI vs human code review comparisons.
Finally, a secure mindset demands an obsessive focus on data integrity. You have to protect data from the moment it enters your system until it's safely stored in your database. This means validating it, sanitizing it, and handling it consistently across its entire journey to shut down entire classes of attacks like injection flaws and data tampering.
This principle is all about scrutinizing the path data takes through your application. A proper code review will check that validation rules applied on the front end are re-validated on the back end. It’s about creating layers of defense, so if one layer fails, another is waiting to catch the threat. This is a crucial element of any serious vulnerability remediation strategies.
By embracing these principles, teams can move past superficial checks and cultivate a genuine, deep-seated culture of security. In the end, this mindset is your single most powerful tool for building software that isn't just functional, but truly resilient.
Not all secure code reviews are created equal. Just like you wouldn't use the same blueprint for a skyscraper as you would for a single-family home, your approach to code review needs to fit your project. Picking the right method is a balancing act between speed, cost, and how deep you need to go.
The three main flavors of code review are manual, automated, and a hybrid approach that pulls from both worlds. Each has its place, and understanding their strengths and weaknesses helps you make a smart call instead of just defaulting to one method for everything.
A manual secure code review is like a seasoned detective meticulously combing through a crime scene. It's slow, deliberate, and relies on deep human expertise. A senior developer or security specialist will actually read through the code line by line, looking for subtle and complex flaws that automated tools almost always miss.
This hands-on approach is fantastic for digging up:
While incredibly thorough, manual reviews are both time-consuming and expensive. They just don't scale well, so you'll want to reserve them for your most critical, high-risk codebases, like payment processing systems or authentication services.
Automated reviews, usually done with Static Application Security Testing (SAST) tools, are the high-speed baggage scanners of the code world. They tear through massive amounts of code in minutes, flagging common, well-known issues with incredible efficiency. These tools scan your source code without even running it, looking for patterns that match known vulnerability signatures.
SAST is your first line of defense against the usual suspects. This infographic shows just how common some of these vulnerabilities are, which is why having an automated check is so crucial.
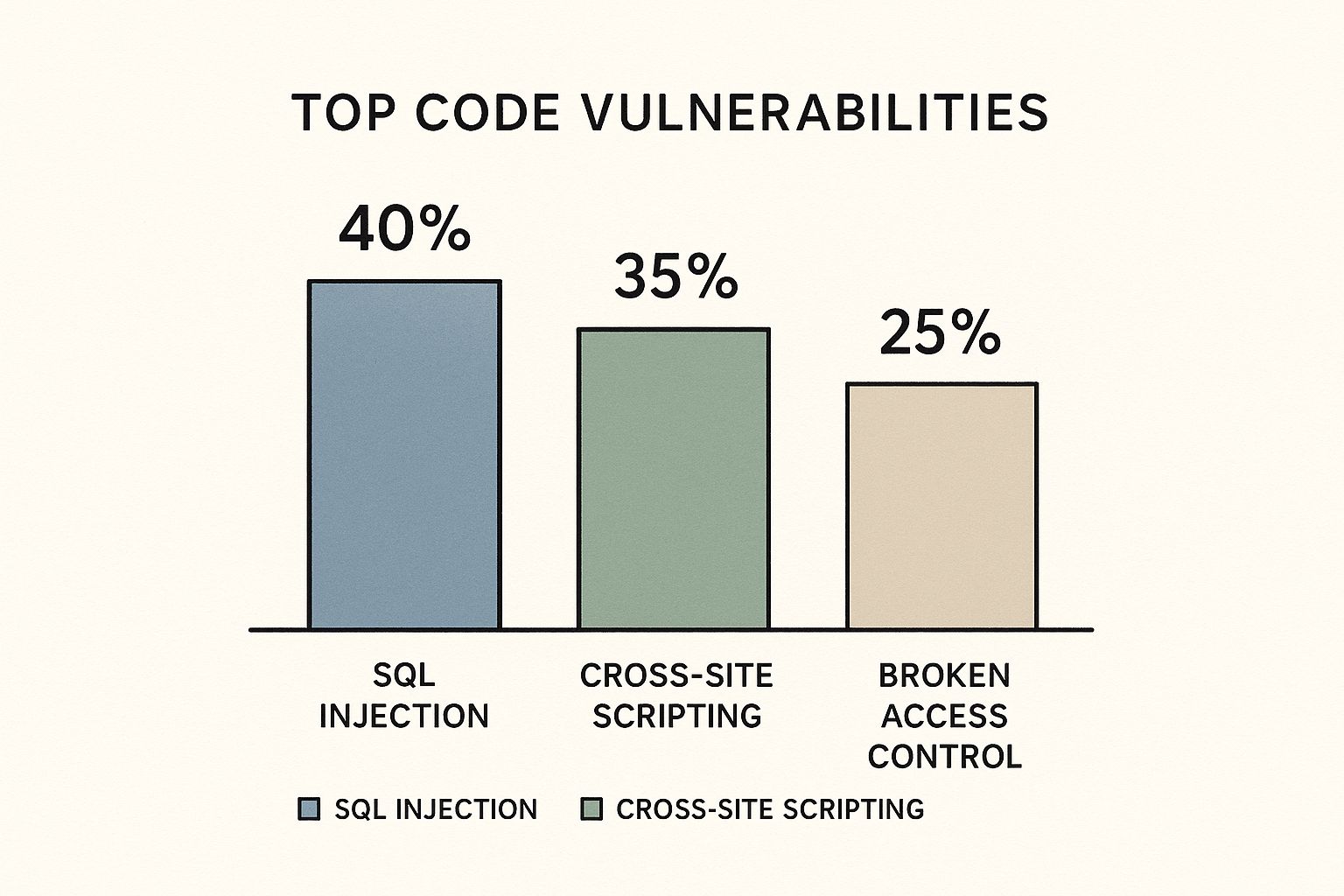
The data makes it pretty clear why you'd want to automate checks for things like SQL injection to maintain a basic security baseline. The downside? SAST tools can be noisy, generating a lot of false positives. They also lack the context to understand business logic, so they'll miss clever or unique flaws. To get a better handle on this technology, check out our guide on what is static code analysis.
For most modern development teams, the hybrid approach is where the magic happens. It combines the raw speed and scale of automated SAST scans with the depth and context of a manual review. This creates a powerful, layered defense that catches both the low-hanging fruit and the more complex, nuanced threats.
A typical hybrid workflow involves running automated scans on every pull request to get instant feedback on common errors. Then, for high-risk changes or brand-new features, a human reviewer steps in to perform a targeted manual review, focusing their expertise where it matters most.
This dual approach has become even more important with the rise of AI-generated code. Shockingly, recent findings show that nearly 45% of AI-generated code contains OWASP Top-10 flaws. Finding these issues early can slash remediation costs by up to 10 times compared to fixing them after release. This blend of automation and human insight gives you comprehensive coverage without grinding your development pipeline to a halt.
To help you decide, here’s a quick breakdown of how the three methods stack up against each other.
Ultimately, for most teams, the hybrid model delivers the best of both worlds, making security both effective and sustainable in a fast-paced environment.
For far too long, security has been treated like a final, painful tollbooth right before release. It shows up at the last minute, flags a bunch of issues, and brings all momentum to a screeching halt. That old way of doing things isn't just inefficient; it creates a culture of friction between developers and security teams.
A truly effective secure code review process isn't a gatekeeper. It’s a seamless part of the development highway, woven directly into the everyday workflow.
The whole idea is to "shift security left." It’s a simple concept that just means moving security checks to the very beginning of the development lifecycle. When you do this, security stops being a reactive bottleneck and becomes a proactive, collaborative effort. It transforms from something to dread into a shared responsibility for building better, more resilient products.
If you're looking for the perfect place to centralize your security efforts, look no further than the pull request (PR). It's a natural pause point where code is already being reviewed for functionality and style, making it the ideal moment to also check for security vulnerabilities.
By integrating security checks right here, you can catch potential flaws before they ever get merged into the main branch. This is where automation becomes your best friend.
Imagine setting up automated SAST scans to run on every single commit or PR. Developers get immediate, actionable feedback right where they work. They can see a potential issue, understand its impact, and fix it on the spot—all while the code they just wrote is still fresh in their minds. This rapid feedback loop is what truly builds and reinforces secure coding habits. You can see exactly how this works by exploring best practices for pull request testing.
Let's walk through what this looks like in the real world during a typical feature development cycle. This process takes security from an abstract idea and turns it into a concrete, repeatable set of actions.
This workflow makes security visible, immediate, and collaborative. It becomes just another part of the team's daily muscle memory.
The most important outcome of this integrated approach is the culture it helps build. When security feedback is delivered constructively right inside the PR, it stops feeling like a personal critique and starts feeling like a team effort to improve the code.
The conversation shifts from "you made a mistake" to "let's fix this vulnerability together."
Security should be built in, not bolted on. When you integrate security checks directly into the development workflow, it becomes a natural part of the creative process, empowering developers to own the security of their code from the very beginning.
To make this feedback loop truly effective, you need clear guidelines for triaging what the tools find. Not every alert from an automated scan is a five-alarm fire. Create a system to classify vulnerabilities by severity—like Critical, High, Medium, and Low—and define what needs to happen for each.
For teams ready to bake security into every stage, exploring comprehensive DevSecOps best practices can provide a solid framework for this cultural shift. By making security a seamless, automated, and collaborative part of your development process, you empower your team to build more secure products, faster.
Knowing the theory behind a secure code review is a great start, but the real test is spotting threats in your own codebase. Time and again, certain vulnerabilities pop up, leaving the door wide open for attackers. If you can learn to recognize these common patterns, your team can shut them down long before they ever see the light of day in production.
Let's put a spotlight on some of the most critical and frequent offenders: SQL Injection, Cross-Site Scripting (XSS), and Broken Access Control. We'll peek at simple code snippets to see what makes them tick and, more importantly, share some cautionary tales of how these seemingly small mistakes led to major security disasters.
SQL Injection (SQLi) is an old-school attack, but it's still devastatingly effective. It happens when an attacker manages to sneak malicious SQL commands into a query that your application sends to its database. If your code isn't prepared, it might just execute those commands, giving the attacker a free pass to all your data.
Here’s a real-world scenario: A small e-commerce startup was thrilled with its new, custom-built search feature. The problem? The developer was just tacking the user's search term directly onto the SQL query string. An attacker figured this out and, instead of a product name, entered a malicious command that bypassed authentication and dumped the entire customer database—names, addresses, and credit card info. The breach was catastrophic, forcing the startup into a costly and brand-destroying recovery.
Let's see how this happens.
Vulnerable Code Snippet (Python):
user_input = request.form['username']query = "SELECT * FROM users WHERE username = '" + user_input + "'"# This is dangerous because an attacker can alter the query's logic.Patched Code Snippet (Python):
user_input = request.form['username']# Using parameterized queries separates data from commands.query = "SELECT * FROM users WHERE username = %s"cursor.execute(query, (user_input,))By using parameterized queries (or prepared statements), you're telling the database to treat user input strictly as data, never as executable code. It’s a simple fix for what could be a company-ending problem.
Cross-Site Scripting (XSS) is a tricky one. It works by tricking a user's browser into running malicious scripts. This happens when your application takes user-supplied data—like a comment on a blog post—and displays it on a webpage without properly cleaning it first. An attacker can inject a script that, when viewed by another user, steals their session cookies or redirects them to a phishing site.
Picture this: A popular social media platform let users customize their profile bios with HTML. A clever attacker embedded a malicious JavaScript snippet in their bio. Anyone who viewed the attacker's profile unknowingly executed the script, which then automatically reposted itself to their own profile. This created a self-propagating "XSS worm" that spread like wildfire, causing chaos and eroding user trust until engineers finally patched the flaw.
The core principle here is simple: never trust user input. Always assume any data coming from outside your application is hostile until you've proven otherwise. Sanitizing and encoding data isn't optional—it's essential.
Vulnerable Code Snippet (JavaScript/HTML):
// A user's comment is inserted directly into the page.const userComment = "<script>alert('You have been hacked!');</script>";document.getElementById('comment-section').innerHTML = userComment;Patched Code Snippet (JavaScript/HTML):
// The user's comment is treated as text, not executable code.const userComment = "<script>alert('You have been hacked!');</script>";document.getElementById('comment-section').textContent = userComment;Using .textContent instead of .innerHTML ensures the browser renders the input as plain text, completely neutralizing any sneaky scripts. For teams looking to get ahead of these issues, understanding effective vulnerability remediation is a must.
Broken Access Control is exactly what it sounds like: your application fails to properly enforce what a user is allowed to do. This flaw lets attackers perform actions or view data that should be off-limits, essentially strolling right past your authorization checks. It's like leaving the door to the admin panel unlocked for anyone to wander through.
One of the most dangerous and related mistakes is accidentally exposing secrets. A recent report found that 61% of organizations have leaked sensitive credentials in public repositories. With 35% of GitHub repositories being public, a single mistake can hand an attacker the keys to the kingdom. You can discover more about these code security findings.
Here's how it plays out: A healthcare startup built a portal for patients to view their medical records. The URL to view a record looked something like /records?id=123. A curious user simply changed the ID number in the URL to 124 and was shocked to see someone else’s private medical information. The system correctly authenticated the user at login but completely failed to verify if that user was authorized to see the specific record they requested. That simple oversight exposed thousands of sensitive patient records.
Tools and processes will only get you so far. When it comes to secure code review, the real magic happens with your people. A truly effective security program isn't about pointing fingers when mistakes are made; it's about building a supportive environment where security is everyone's job.
The goal is to empower your team to build safer products from day one.
This all starts with how feedback is delivered. The golden rule is to critique the code, not the coder. When reviews are framed as a collaborative learning opportunity, they build trust. Developers start proactively looking for security best practices instead of just trying to avoid getting in trouble.
One of the best ways to scale security knowledge is by launching a security champions program. Think of these as developers on your existing teams who are genuinely curious about security. You give them a little extra training and support, and they become the go-to person for their peers.
These champions act as a bridge between the core development teams and any dedicated security folks. They can answer questions, promote better habits, and help embed security directly into the daily workflow. It stops security from feeling like an outside force and makes it a natural part of how the team works.
A strong security culture has to be built on continuous learning. Threats change constantly, and your team’s knowledge needs to keep up. This doesn’t mean you have to book expensive, week-long training courses.
It can be much simpler and more effective:
To back this up, standardized checklists are your best friend. A solid checklist makes sure every secure code review hits the critical points, like checking for injection flaws or making sure access controls are right. This brings consistency to the process without killing creativity, giving reviewers a reliable framework to follow. You can dive deeper into some foundational software development security best practices to get started.
Security is not a feature you add at the end; it's a quality you build in from the beginning. A culture of secure development ensures that this quality is woven into every line of code, every feature, and every product decision your team makes.
When you get the culture right, security stops being a roadblock and becomes a shared mission. It’s an acknowledgment that everyone on the team plays a part in protecting the product and its users. This collaborative mindset doesn't just cut down on vulnerabilities—it leads to better code and more resilient applications. Investing in your people is the most powerful and lasting defense you can build.
Jumping into a formal secure code review process can bring up a lot of questions for development and product teams. It's a shift in mindset, and it's natural to wonder how it all fits together. We’ve heard them all, so here are some answers to the most common ones we get from teams just like yours.
Think of secure code review less as a one-off gate before a big release and more as a constant, humming part of your development engine. To really nail it, you want to weave it right into your daily workflow.
What does that look like in practice?
Security is everyone’s job, but you still need a point person. Often, a senior developer or a designated "security champion" takes the lead. But don't underestimate the power of peer reviews—having developers check each other's code is fantastic for catching errors and spreading security knowledge across the team.
If there's one golden rule, it's this: the person who wrote the code should never be the one reviewing it. You absolutely need a fresh set of eyes to spot the subtle mistakes, flawed assumptions, and logic gaps the original author is bound to miss.
This is the big one, isn't it? It’s a totally valid concern. And yes, there can be a slight adjustment period at the beginning. But here's the truth: building security in from the start actually makes you faster in the long run.
Think about it. Finding and fixing a vulnerability while you’re still coding is infinitely cheaper and quicker than scrambling to patch a live product after a breach.
Modern tools and a well-oiled process remove most of the friction. When you make security a seamless part of your CI/CD pipeline, it just becomes another quality check—one that prevents massive, costly delays down the road instead of causing them.
Ready to make your code reviews faster, smarter, and more secure? With Sopa, you can automate checks, get AI-powered insights, and build a stronger security culture without slowing down your team. Start your free trial of Sopa today and see the difference.
