Discover 8 essential software development security best practices. Our guide offers actionable insights for dev teams to build secure applications.
In today's fast-paced development world, shipping features quickly is the goal. But what happens when speed comes at the cost of security? Imagine a hot new fintech startup launching its app, only to suffer a massive data breach a week later because of a simple, preventable bug. That one vulnerability can destroy user trust, cost millions, and grind your roadmap to a halt. The truth is, security isn't a final checkbox; it's a foundational part of quality software. Integrating strong software development security best practices from day one is the most effective way to build resilient, trustworthy products.
This guide moves beyond theory to give your product and development teams a practical, actionable roadmap. We'll explore 8 critical practices, backed by real-world examples, that will help you embed security into your team's DNA, protect your users, and ultimately, ship better software, faster. Let's dive into how to make your development lifecycle secure by design, not by accident. You'll learn how to implement everything from "shifting left" to securing your dependencies, ensuring your application is fortified at every stage.
Think of traditional security like a single, stressed-out bouncer at the front door of a massive nightclub, trying to check everyone's ID right at the end. It's slow and problems are discovered way too late. "Shift-Left Security" is like having friendly security guards helping out much earlier in the process—checking things as people design the party, set up the decorations, and even as they're walking down the hall. It means integrating security checks as early as possible in the development lifecycle. Instead of waiting until the end, this approach, often called DevSecOps, makes security a shared responsibility for everyone on the team.
By "shifting left," teams find and fix security issues when they are easiest and cheapest to fix: right when the code is being written. This is much better than finding a major flaw right before a big launch, which can cause panic, costly delays, and complex fixes. Implementing software development security best practices from the start ensures that applications are built on a secure foundation, significantly reducing risk.
Adopting a shift-left mindset transforms security from a roadblock into a smooth, integrated part of your workflow. The core idea is to automate security checks and empower developers with the tools and knowledge to write secure code from the get-go.
The following infographic highlights the quantifiable benefits of adopting this approach.
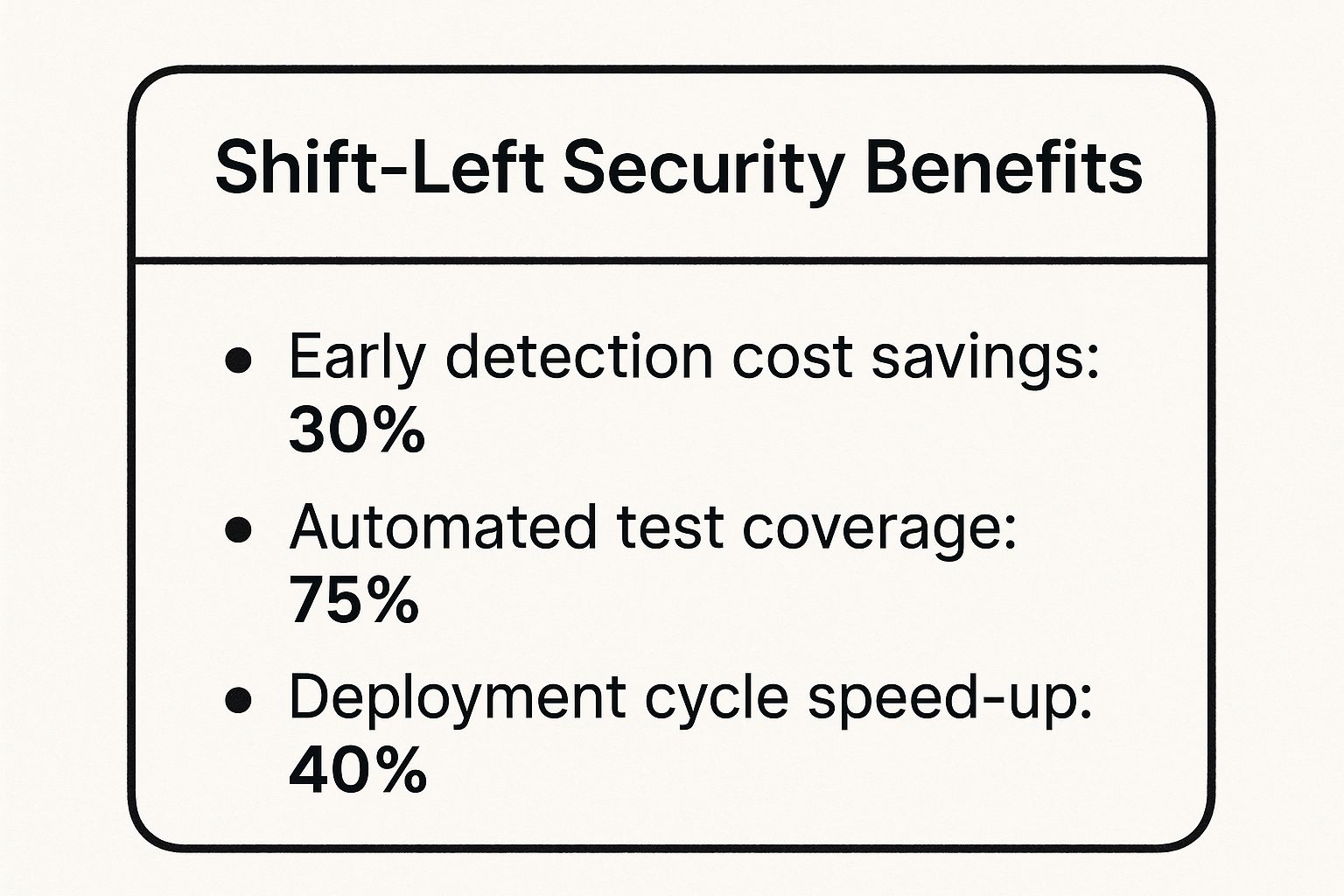
As the data shows, the impact is substantial, leading to faster, more efficient, and more secure development cycles. Companies like Netflix and Microsoft have successfully pioneered these practices, proving that building security in, not bolting it on, is the most effective strategy. You can learn more about how to implement shift-left testing practices for your team.
A secure code review is like having a skilled editor proofread an important document for errors before it gets published. It's a systematic check of the application's source code to find and fix security weaknesses. This is done through a combination of automated tools (Static Application Security Testing, or SAST) and manual reviews by other developers. The goal is to catch issues like injection flaws or insecure data storage before the code ever makes it into the final product.
This two-pronged approach is powerful. Automated tools are great at quickly scanning huge amounts of code for well-known types of mistakes. But a human reviewer can spot complex logical errors that a tool might miss—for example, a flaw in a checkout process that an automated scanner wouldn't understand. By making this a standard step, you ensure software development security best practices are consistently followed and security becomes a normal part of ensuring code quality.

Integrating secure code reviews and static analysis creates a powerful, multi-layered defense right at the code level. It helps developers learn from mistakes in real-time and builds a culture where everyone is responsible for security, similar to how teams at Google and Salesforce approach it.
This systematic approach makes security reviews a productive and educational part of the development cycle rather than a bottleneck. You can explore how modern tools are enhancing this process by learning more about AI-powered code review tools and their capabilities.
Imagine your app has a sign-up form. Input validation is like a rule that says the "email" field must actually contain an email address, and the "age" field must be a number. It's the practice of treating all data from the outside world as potentially harmful until it's been checked. This involves rigorously checking, filtering, and cleaning any data your application receives—from a user form, an API call, or a file upload—before it's used or stored.
By setting up strict rules for what is considered acceptable input, developers can block a huge range of common attacks, such as SQL injection (where an attacker tries to sneak database commands into a search bar) or Cross-Site Scripting (XSS). This is one of the most fundamental and effective software development security best practices for protecting your app from malicious data. It's a non-negotiable step for protecting your system and your users.
Adopting a strict input validation strategy turns potential entry points for attackers into fortified checkpoints. The core idea is to define and enforce data rules on both the user's browser (client-side) and your server (server-side) for multiple layers of defense.
Frameworks like Ruby on Rails and Django have these practices built into their core, proving their effectiveness. By validating every piece of incoming data, you build a resilient application that is inherently more secure.
The Principle of Least Privilege (PoLP) is a simple but powerful idea: a user or a piece of software should only have the bare minimum permissions necessary to do its job. Think of it like giving a valet a key that only starts the car and opens the driver's door, not a master key that also opens the trunk and the glove box. In software, this means an application service should only have permission to read the data it needs, not the entire database.
This approach dramatically shrinks your "attack surface." If a part of your system with very limited permissions gets compromised, the attacker is stuck. They can't do much damage because the component they control has no access to anything important. Adhering to this principle is a critical part of modern software development security best practices, especially in complex systems like cloud apps and microservices where many different parts are talking to each other.
Implementing the Principle of Least Privilege shifts your security from a "let everyone in and then lock doors" model to a much safer "no one gets in unless they have a specific invitation" model. The goal is to grant permissions deliberately, not just remove them when something goes wrong.
Authentication and authorization are the digital bouncers for your app. Authentication is the process of confirming someone is who they say they are—like checking their ID at the door. Authorization is what happens next: deciding what that person is allowed to do once they're inside—like whether their ticket gets them into the VIP section. Getting these two things right is a critical software development security best practice to prevent unauthorized access and data breaches.
A small mistake in either process can put your entire application at risk. For example, a weak password policy could let an attacker easily guess a user's password. Or a bug in your authorization logic could let a regular user access the admin dashboard. By using strong, industry-proven methods, you can ensure that only the right people can access the right things.

Properly implementing authentication and authorization protects you from some of the most common and damaging security threats. The goal is to create a secure, smooth user experience without cutting corners on security. This is often best done using trusted services like Auth0, Okta, or Firebase Authentication.
httpOnly cookies for session tokens, which prevents them from being stolen by malicious scripts. Make sure sessions expire after a reasonable time and that logging out properly invalidates the session on the server.By building these controls into your app from the start, you create a strong defense against unauthorized access, protecting both your users and your company.
Secure data handling and encryption are essential for protecting sensitive information, whether it's sitting in a database (at rest) or moving over the internet (in transit). Encryption scrambles data so that it's unreadable to anyone without the right key. By using strong encryption, you ensure that even if an attacker manages to intercept data or break into your servers, the information they get is just a useless jumble of characters.
This isn't just an extra layer of security; it's a core part of a "defense-in-depth" strategy for protecting your most valuable asset: your data. Implementing robust software development security best practices for data handling is crucial for earning user trust and complying with privacy laws like GDPR. Good security starts with understanding data breaches and prevention strategies.
Effective data protection requires a combination of strong encryption methods, secure key management, and clear policies for handling data. The goal is to make data protection an automatic, default part of your system, not something you have to remember to do.
Apps like Signal and WhatsApp are famous for their strong end-to-end encryption, which has built massive user trust. Similarly, cloud storage services like Dropbox use encryption to ensure that even their own employees can't access user files, making data security a core product feature.
Modern software is built like a house from pre-fabricated parts, not from scratch. These "parts" are third-party libraries and open-source packages that developers use to save time. Dependency and supply chain security is all about making sure these third-party components are safe. A single vulnerable library can be like a faulty part that brings down the whole house.
An attacker can exploit a vulnerability in a popular open-source library to attack every application that uses it. High-profile incidents like the SolarWinds attack showed how attackers can inject malicious code into trusted software updates. This means implementing software development security best practices for your dependencies is no longer optional—it's essential for protecting your software from a huge and growing attack vector.
Carefully managing your dependencies protects your app from inheriting security flaws and ensures the integrity of your code. The goal is to get a clear picture of what third-party code you're using and automate the process of keeping it secure and up-to-date.
package-lock.json). This ensures that your builds are always consistent and prevents a library from automatically updating to a new, potentially insecure version without you knowing.This proactive approach turns supply chain security from a chore into an integrated part of your development process, strengthening your app's security from the ground up.
Security testing is the process of actively trying to break your own application to find security weaknesses before an attacker does. This goes beyond simple checks and involves using a range of methods to simulate real-world attacks. By proactively finding and fixing flaws, teams can ensure their software is resilient, making this one of the most important software development security best practices.
This process is multi-faceted. It includes static analysis (SAST) to check the raw code, dynamic testing (DAST) to test the running application, and sometimes manual penetration testing, where a security expert tries to hack the system. To effectively find and fix potential weak spots, it's key to have a solid understanding what vulnerability assessment entails. This knowledge helps teams prioritize risks and build a strong, layered defense.
Implementing a structured security testing program turns security from a reactive scramble into a proactive, continuous cycle of improvement. It gives you clear evidence of your app's security health and tells you exactly where to focus your fixing efforts.
Companies like Mozilla and Shopify have built world-class security programs around these principles. Mozilla's intense security testing for its Firefox browser and Shopify's program to protect millions of online stores show how a layered testing strategy can effectively protect users at a massive scale.
Building modern software is about more than just shipping cool features; it's about building resilience. The path to strong application security isn't about buying a single tool or running a last-minute scan. It's about a fundamental shift in culture and process. The journey starts when you stop treating security as an afterthought and start treating it as a core part of the software development lifecycle.
All the practices we've discussed, from "shifting left" to securing your dependencies, point to one key idea: proactive prevention is always better, cheaper, and more effective than reactive repair. By embedding security into every phase of development, you turn it from a roadblock into a quality booster. This doesn't just lower the risk of a costly breach; it helps you build better, more reliable software that earns user trust and protects your brand. Integrating these software development security best practices is a powerful competitive advantage.
To turn these ideas into action, focus on these three pillars:
Mastering these concepts is no longer optional in today's digital world. It's the foundation upon which successful, trustworthy products are built. The next step is to move from reading to doing. Start small: pick one area, like automating dependency checks or formalizing your code review process, and build momentum from there. The goal is to make the secure way the easy way for your developers. By embedding these software development security best practices into your team's daily habits, you build a powerful, self-reinforcing security posture. This is how you stop chasing vulnerabilities and start building security in from the very first line of code. Explore how Sopa can specifically help with automated code review use cases.
Ready to make secure coding an effortless part of your team's workflow? Sopa integrates directly into your pull requests, providing automated security feedback and fixes before code is ever merged. Start your free trial today and see how easy it is to implement best practices without slowing down development.
